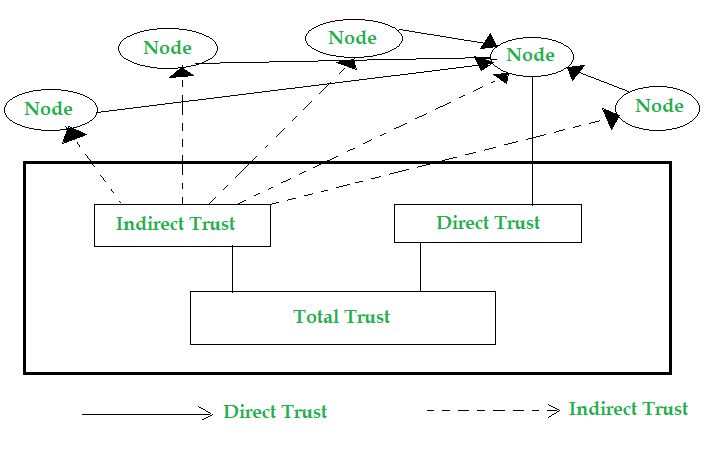
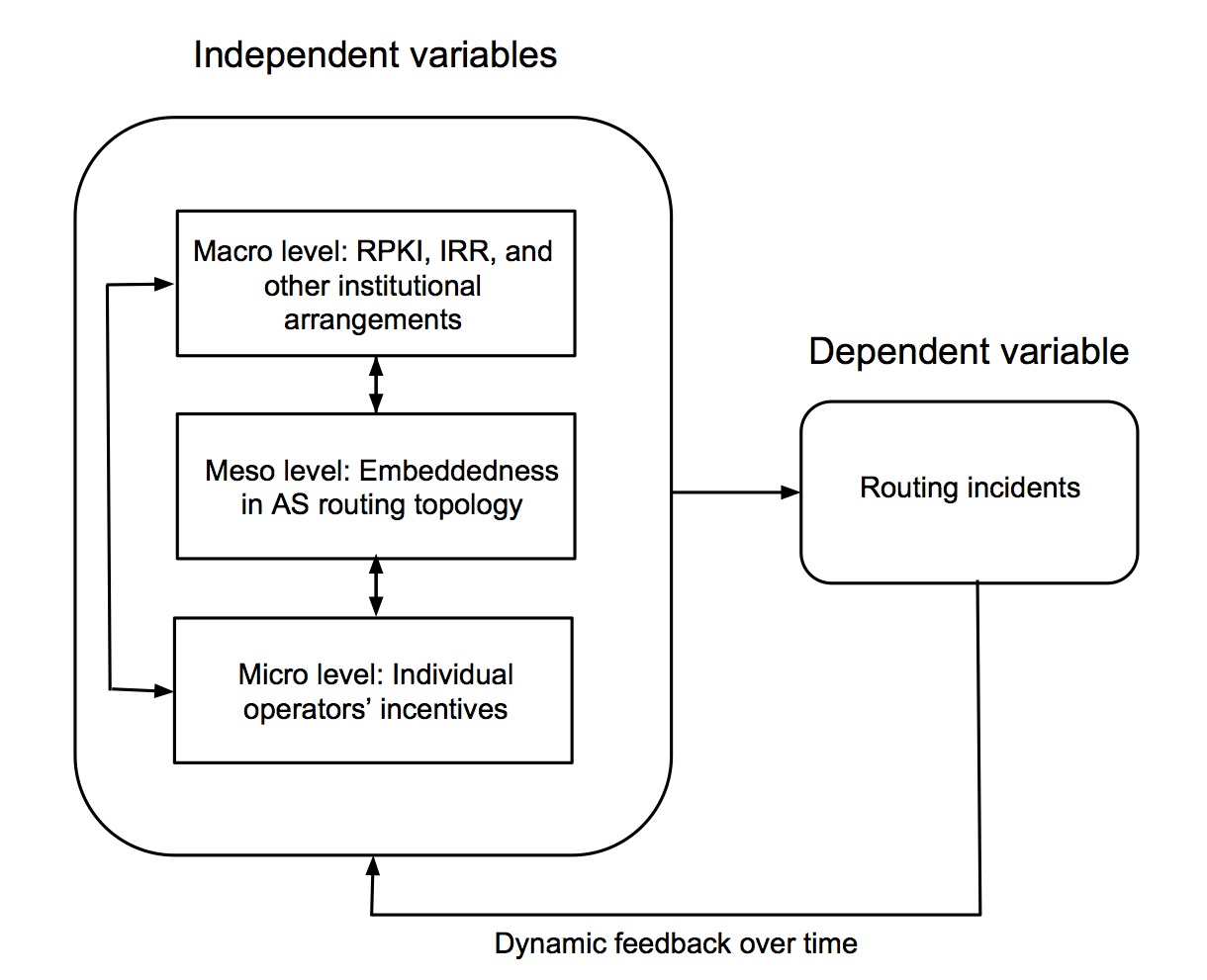
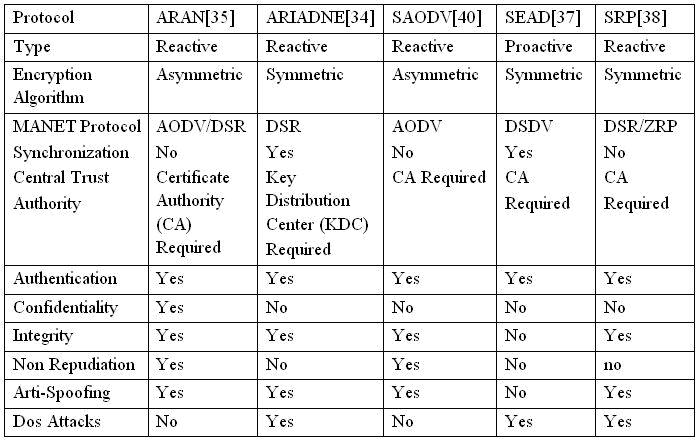
Securing WBAODV Routing Protocol in MANETs: Towards Efficient and Secure Routing Protocol: Elmasry, Wisam: 9783659268793: Amazon.com: Books

RETRACTED ARTICLE:An optimized distributed secure routing protocol using dynamic rate aware classified key for improving network security in wireless sensor network | Journal of Ambient Intelligence and Humanized Computing

Table 4.1 from An Efficient Security Aware Routing Protocol for Mobile Ad Hoc Networks | Semantic Scholar

Secure Multipath Routing Protocols in Wireless Sensor Networks: A Security Survey Analysis | Semantic Scholar

EODBSR: ENHANCED ON-DEMAND BYZANTINE SECURE ROUTING PROTOCOL: For better Throughput and Delivery Ratio: Baratam, Santhosh Kumar: 9783639285727: Amazon.com: Books
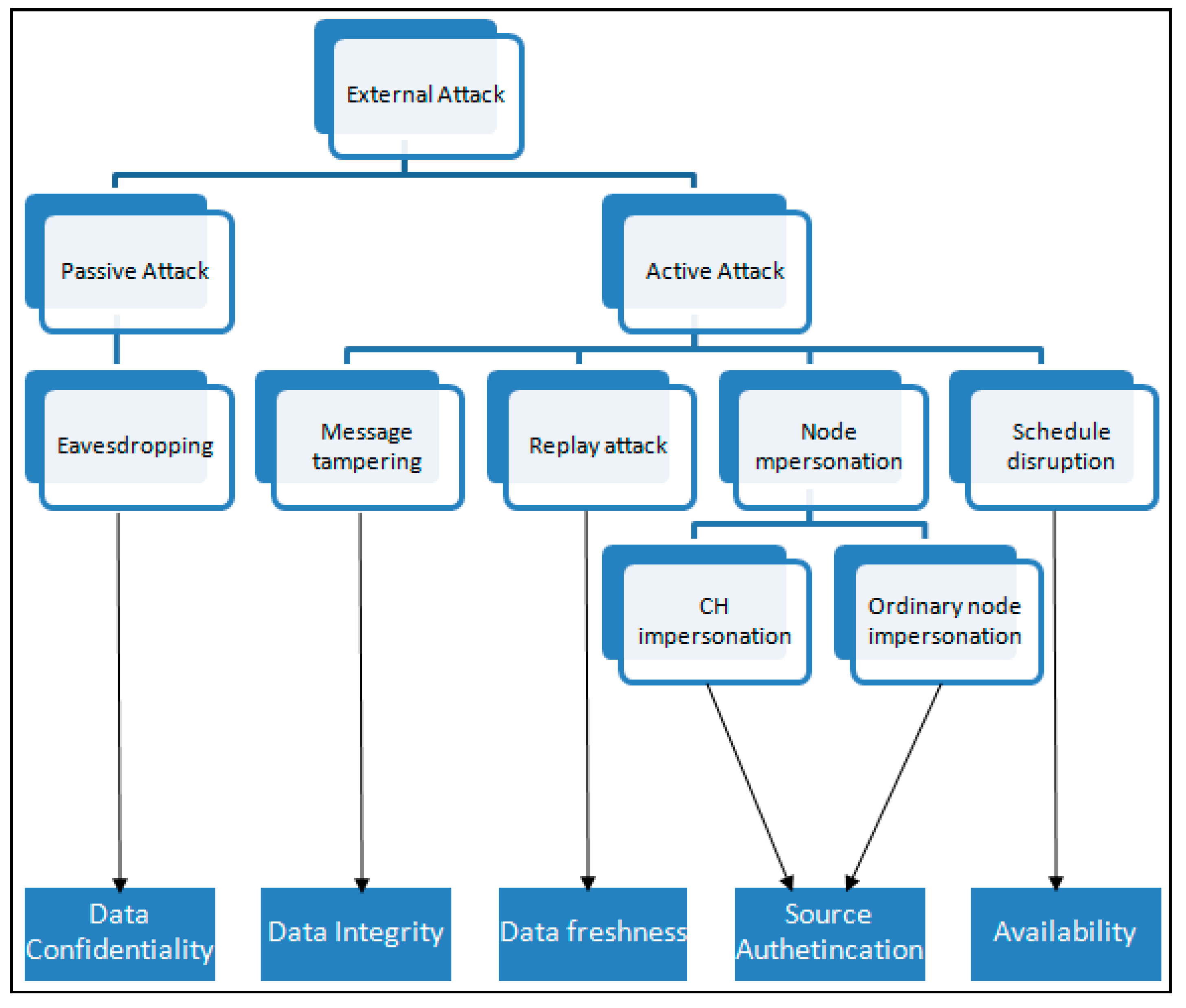
Sensors | Free Full-Text | A Secure Routing Protocol for Wireless Sensor Networks Considering Secure Data Aggregation

Challenges and Developments in Secure Routing Protocols for Healthcare in WBAN: A Comparative Analysis | Wireless Personal Communications

Hierarchical energy efficient secure routing protocol for optimal route selection in wireless body area networks - ScienceDirect

Trust-based secure routing and message delivery protocol for signal processing attacks in IoT applications | The Journal of Supercomputing
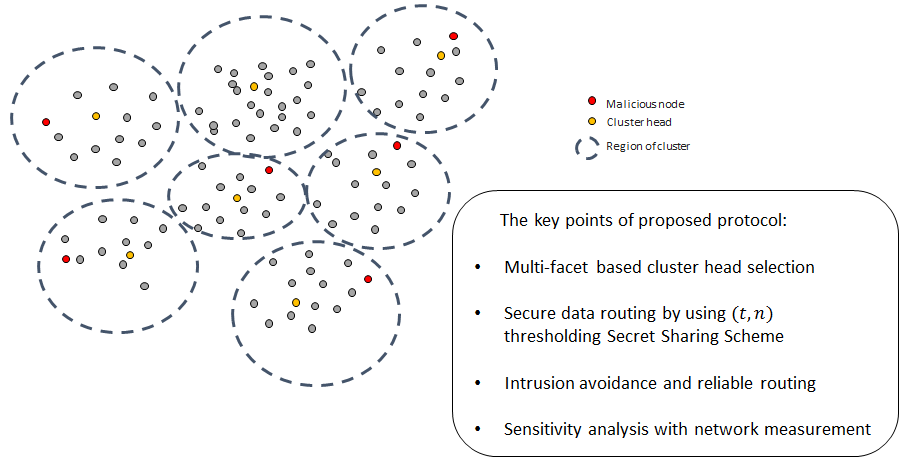
Energies | Free Full-Text | An Energy-Efficient and Secure Routing Protocol for Intrusion Avoidance in IoT-Based WSN